The PortSwigger WebSecurity Academy
The PortSwigger WebSecurity Academy is a great way to learn more about web security, but not too surprisingly it is also intended as a showcase for Burp Suite.
However you can of course use ZAP instead of Burp, and in this series of ZAP Blog posts I will show you how.
The first lab has the tag PRACTITIONER and you can find it here. I want to show you how to solve this lab using ZAP and specifically the Fuzzer tool.
Lab instructions
This lab’s password change functionality makes it vulnerable to brute-force attacks. To solve the lab, use the list of candidate passwords to brute-force Carlos’ account and access his “My account” page.
- Your credentials: wiener:peter
- Victim’s username: carlos
- Candidate passwords
From the instructions it is clear we are going to use a brute-force attack - the Fuzzer is perfect for this.
Manual Testing
After logging into to your account with the provided credentials (wiener:peter) we can see we can update our password:
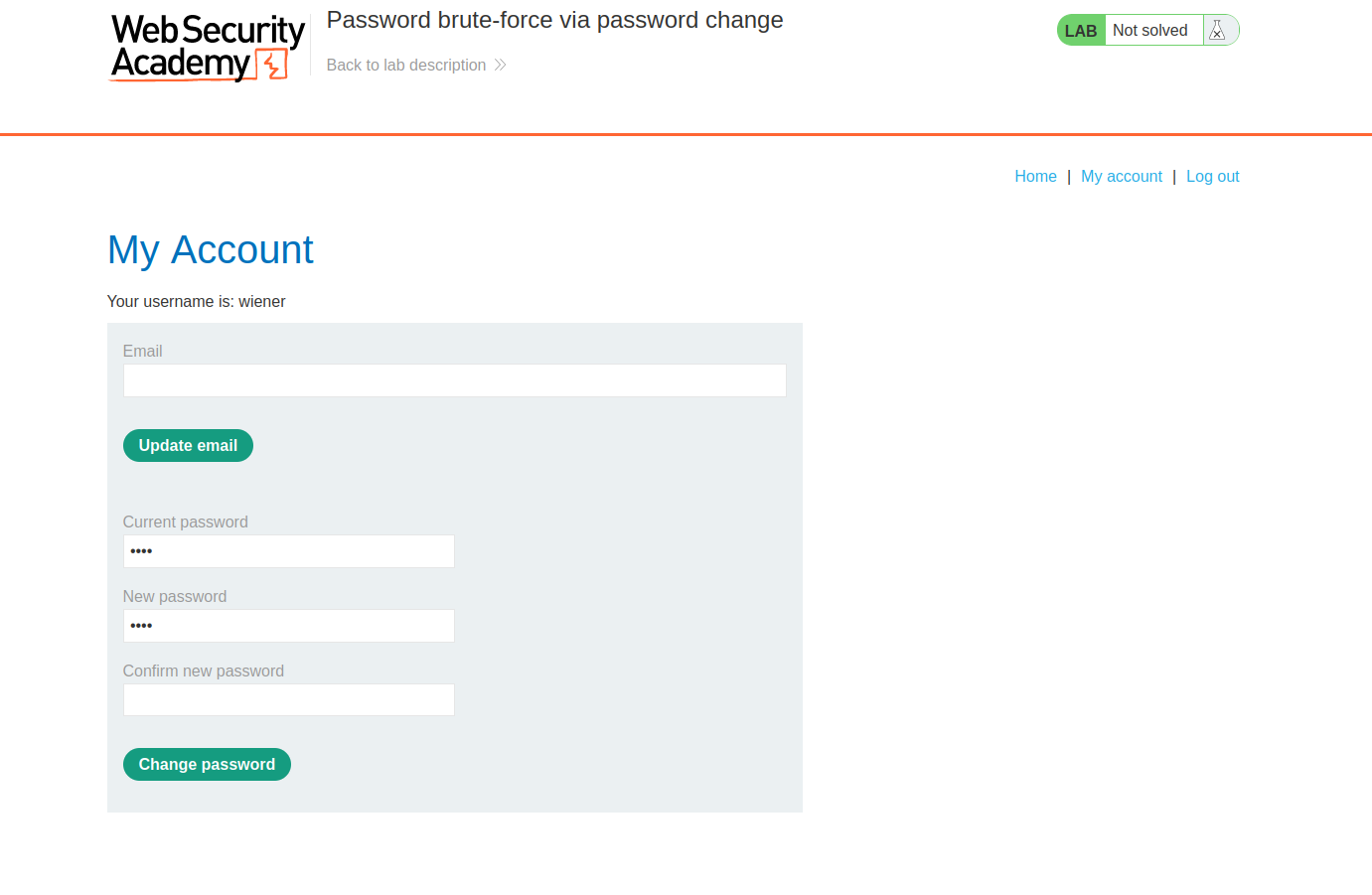
After manually testing this functionality you will find out two important things:
- When you try to Change Password where Current Password is not correct you are redirected to the login page.
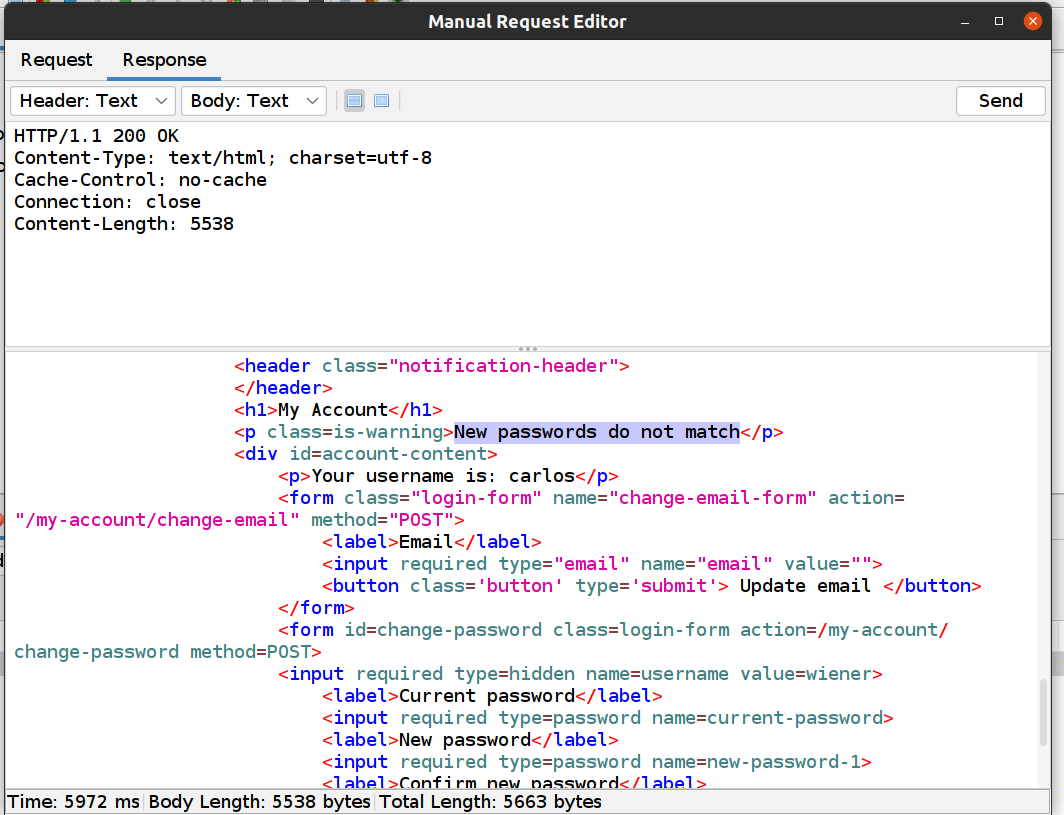
- When you try to Change Password where Current Password is correct but New Password and Confirm New password does not match you will get the error message “New passwords do not match”:
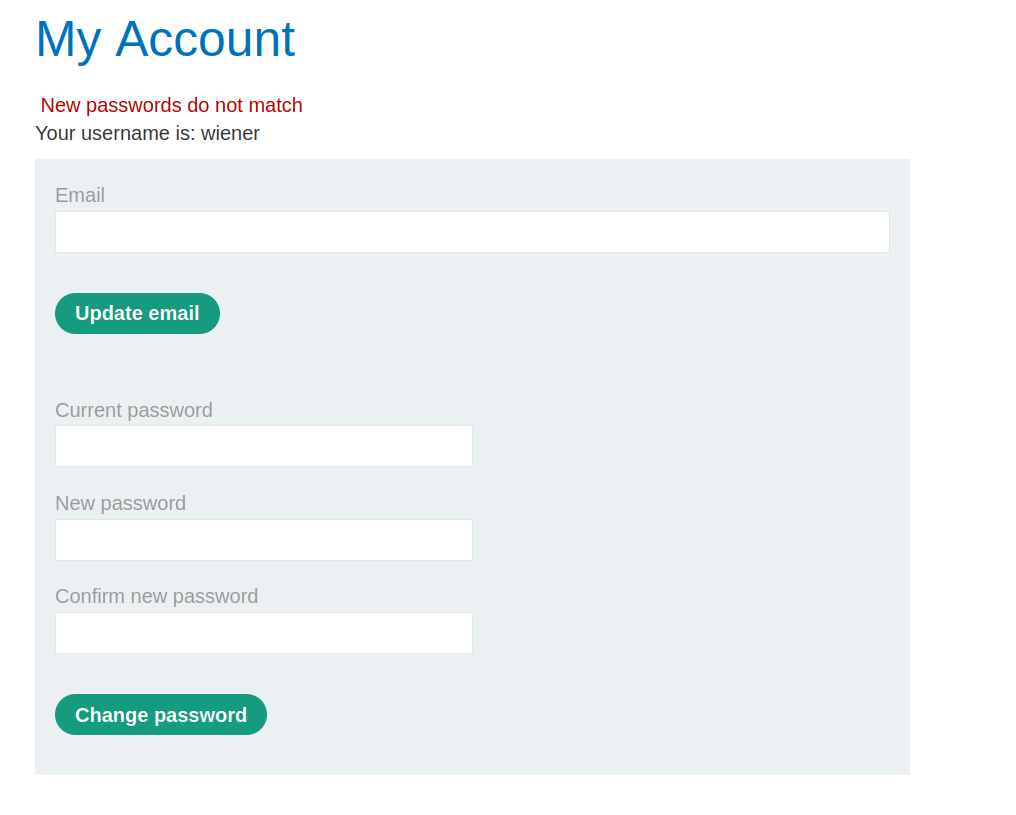
So that means you need to look for the error message “New passwords do not match”. We can use this message to enumerate correct passwords for Carlos’ account.
Attacking with ZAP
- Copy all of the passwords from here
- In the ZAP Sites tree find POST:change-password()
- Right click and Attack->Fuzz …
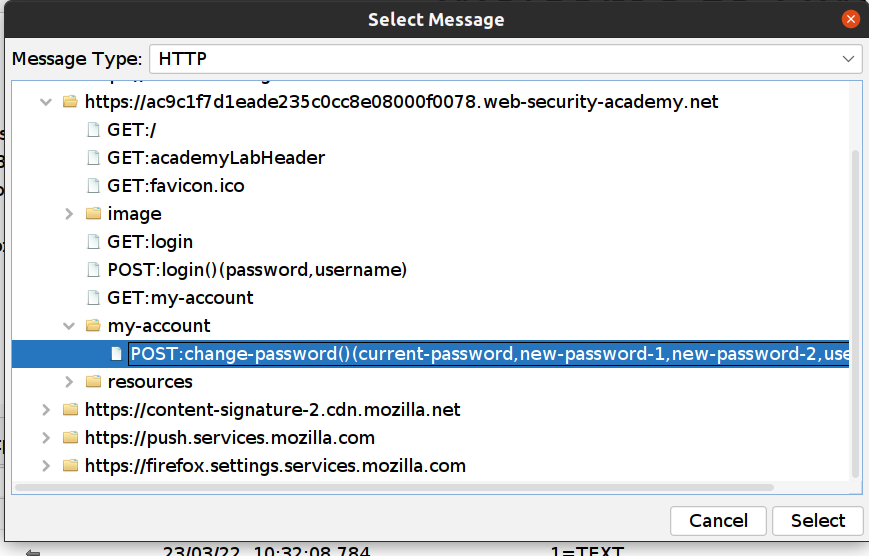
- Highlight the current-password value:
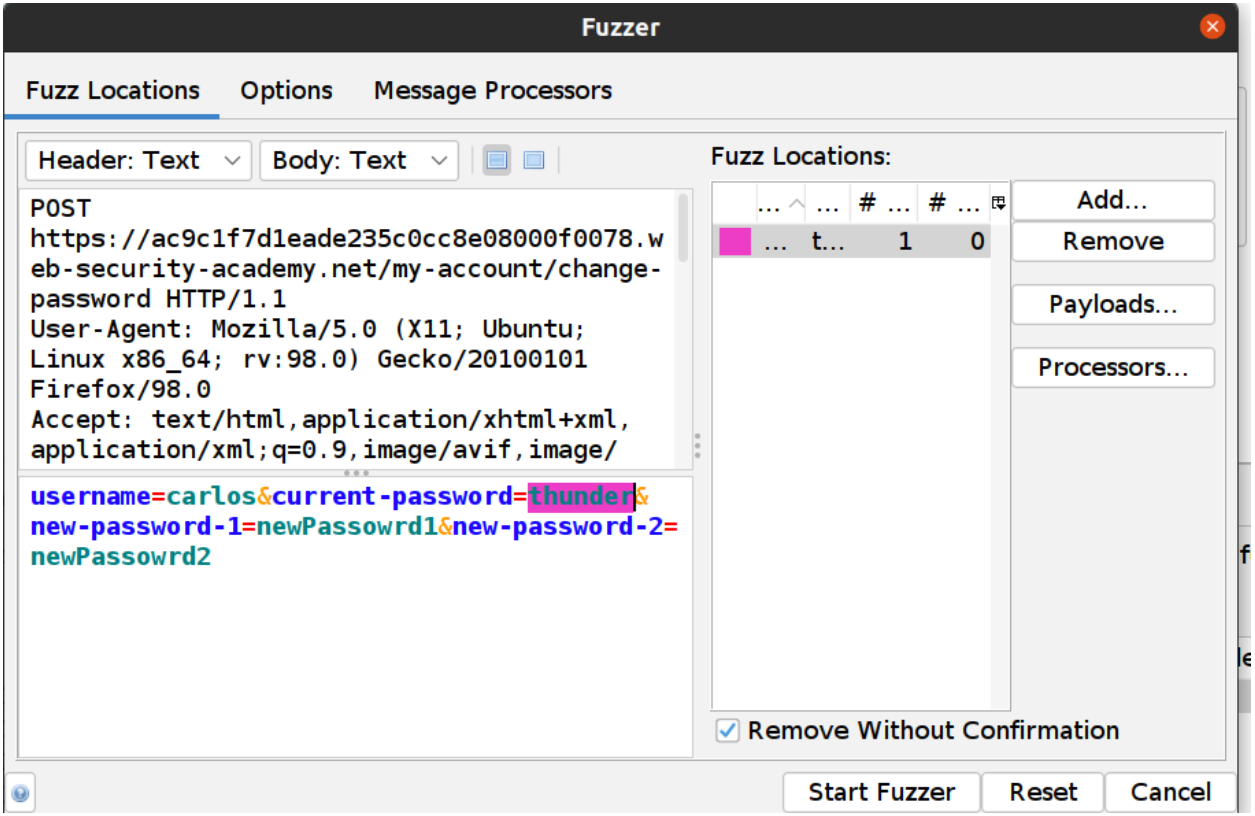
- Click on the Fuzz Locations dialog “Add…” Button
- In the Payloads dialog click on the “Add…” button
- Select Strings (the default) and paste all passwords you copied above
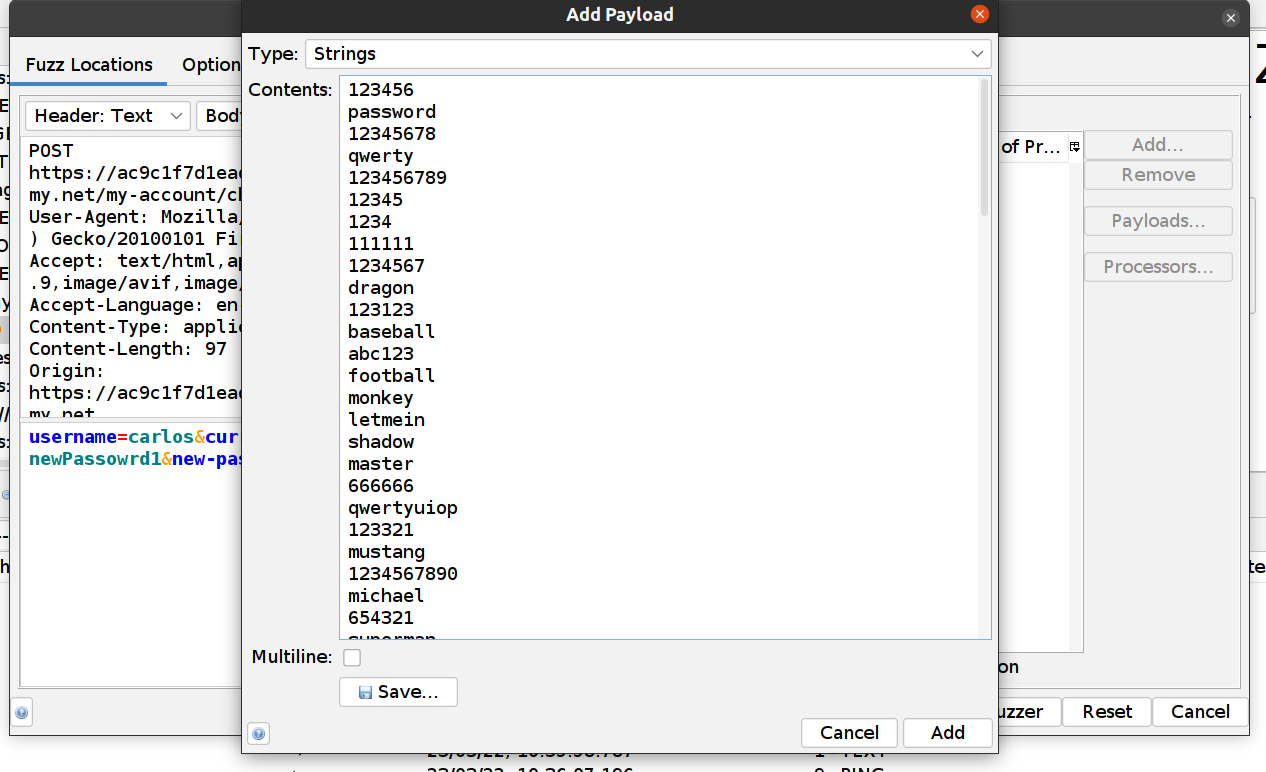
- Click on the Add Payload dialog “Add” button
- Click on the Payloads dialog “OK” button
- Click on the “Start Fuzzer” Button
The requests will be shown in the “Fuzzer” tab at the bottom.
When an attack is done you can notice that one message has a different Size Resp. Body than the rest of the messages.
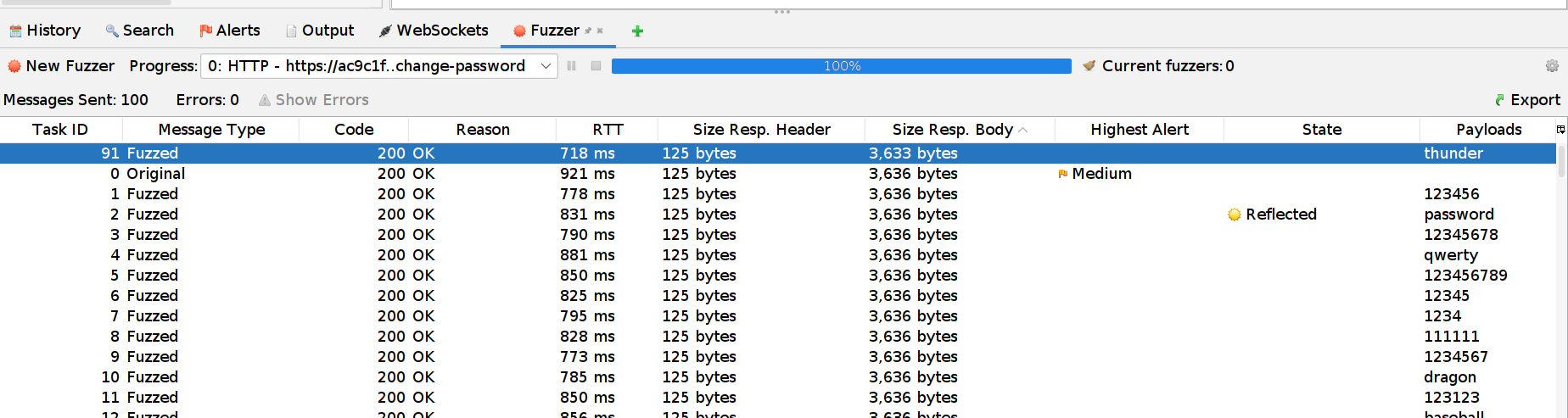
With a closer look we can see the response:
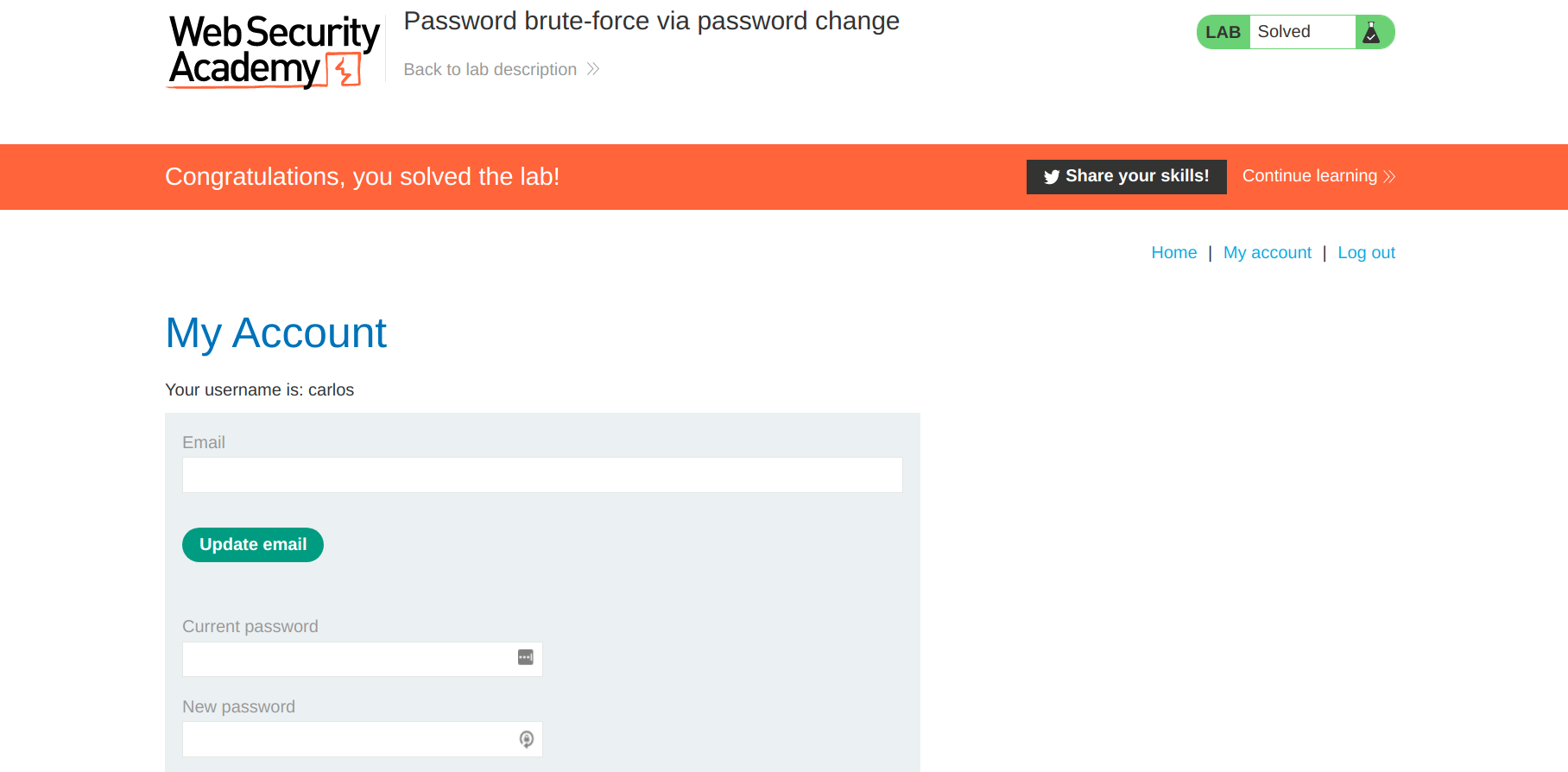
When you now try to login to your account with the new credentials the lab will be solved 😄.
ZAP rocks! 🤘